
Malware Classification System

|
|
Malware Classification System |

|
This topic describes different Types of Malware encountered in IT, IACS and OT environments and the potential risks each may present.
This table indicates the relative risk that each malware type may present in IT, IACS, and OT environments.
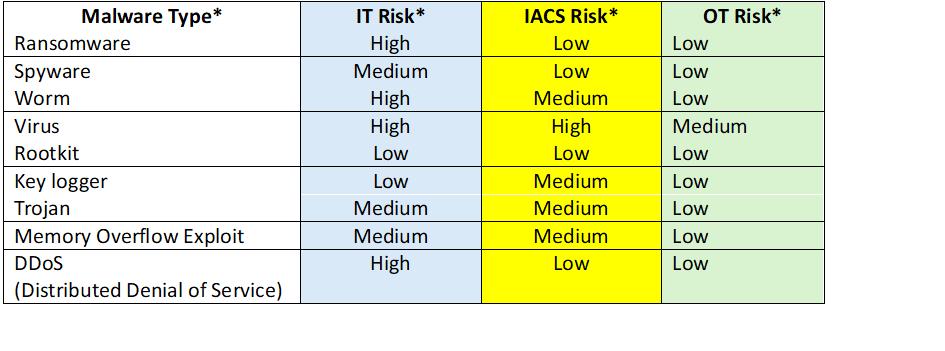
IT and IACS may be distinguished by the architectural levels where they are found. Specifically IT systems are found above the plant industrial firewall(s), and IACS are found at architectural levels below the plant firewall.
However, this is not the case with OT systems which exist at architectural levels above and below the plant firewall. However, OT systems are distinguished by the fact that they require the cooperation of both IACS and IT personnel to design, support, and maintain. It is therefore recommended that this distinction be useed as the definition of OT systems.