
What is a Cybersecurity Program?

|
|
What is a Cybersecurity Program? |

|
Its deliverables include a Master Plan Report, and a number of secondary projects to implement "Opportunities" identified by the Corporate Cybersecurity Master Plan. These secondary projects typically include one or more corporate implementation projects and at least one cybersecurity implementation project for each plant site.
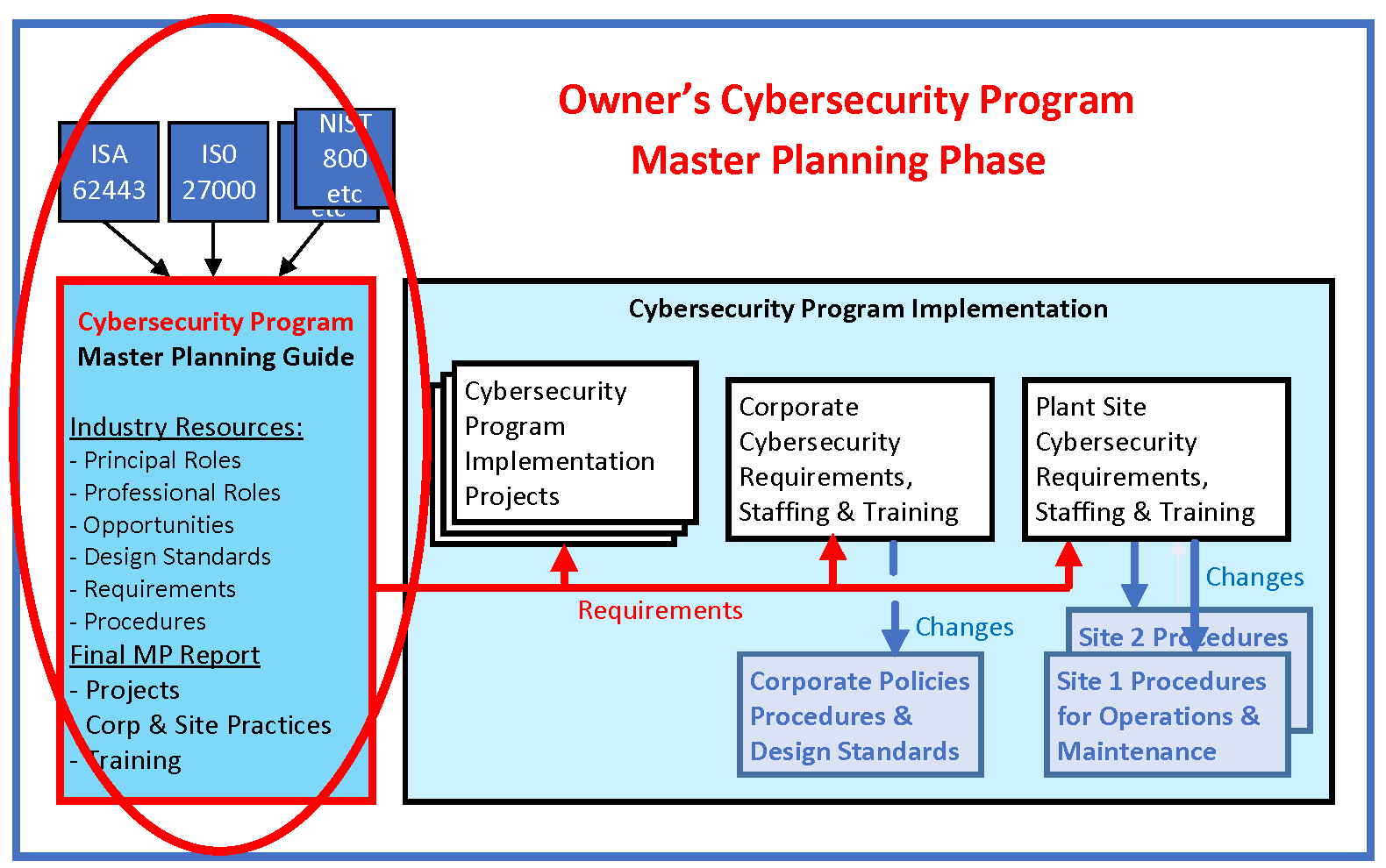
The PERA Master Planning methodology is particularly well suited to carrying out such a Corporate Cybersecurity Master Plan. PERA is widely used for system integration projects and its work processes take special care to clarify human and organizational requirements.
A custom PERA Program Master Planning Guide (shown in light blue) is developed for each industry type. It includes standards, terminology, Professional Roles, improvement Opportunities, and key vendor products that are relevant to that industry and geography.
This Program Master Planning Guide references established cybersecurity standards (shown in dark blue) such as:
Note that example "Deliverables" from the Cybersecurity Master Plan are shown (in the large powder-blue box above). Once these Deliverables have been established by the approved Cybersecurity Master Plan, they are specified by all subsequent projects and operations at Corporate or Plant Site Levels.
As work progresses "Approved Corporate Policies and Practices" are established (first grey box).
Similarly at the next level of detail, "Approved Corporate Procedures and Design Standards" are selected (second grey box).
Finally, Site Operating Procedures and tasks are identified (in keeping within Corporate Policies and Practices). In the case of large differences between sites, practices, procedures and even organizations may require site-specific adaptations.
Click here to download a Cybersecurity Program Master Planning Guide This Guide is a printable or reproduceable pdf file.
Click here to watch a video describing how to use this guide. The PDF and MPEG files may be opened (in adjacent browser windows) allowing the viewer to watch the video while having the slides and written narrative open and independantly scrollable.