
Cybersecurity Master Planning User Guides for
- Process Industry

|
|
Cybersecurity Master Planning User Guides for
|

|
The intent is that experienced Managers, Engineers, and Systems Integrators in a given Industry use these PERA Master Planning Guides to produce a Cybersecurity Master Plan for their enterprise.
These diagrams show important interfaces between each of these 4 Principal Roles in an industry. Interfaces are the most challenging part of enterprise integration, and PERA User Guides helps each organization to define:
The process begins with the Owner/Operator.
Using Master Planning User Guide 1, the Owner selects cybersecurity standards that it will include in its Operating practices and procedures.
Examples might include:
User Guide 1 describes the production of a Cybersecurity Master Plan for that Owner/Operator's enterprise, including reconciliation of conflicting or inapplicable standards, selection of Opportunities, Costs and Benefits, Implementation Projects, training, etc., as described in "What is PERA Master Planning".
User Guides 2, 3, and 4, are used by EPCs, Vendors, and Service Providers (respectively) to create their own Cybersecurity Master Plans. The Deliverables in these plans correspond to the requirements of a Process Industry Owner/Operator. These include specification sheets, Architecture Diagrams, and definition of Professional Roles responsible for creating or responding to Deliverables.
Ideally, EPCs, Vendors and Service Providers will have already produced their own Cybersecurity Master Plans. Several Process Industry EPCs and Vendors already have such plans to match requirements of their main clients. However, if they have not, Deliverables corresponding to Owner/Operator requirements must be agreed before beginning any project or contract.
Each section below also shows a link to an example User Guide for the main enterprise phases of that organization (e.g. Master Planning, Implementation, Operation and Maintenance/Upgrade).

PERA User Guides are available for Process Industry Owner/Operators including:
Each User Guide provides a list of relevant standards, Professional Roles, Typical Opportunities, example Master Planning Reports and other "starter materials" to help with creating the Master Plan.
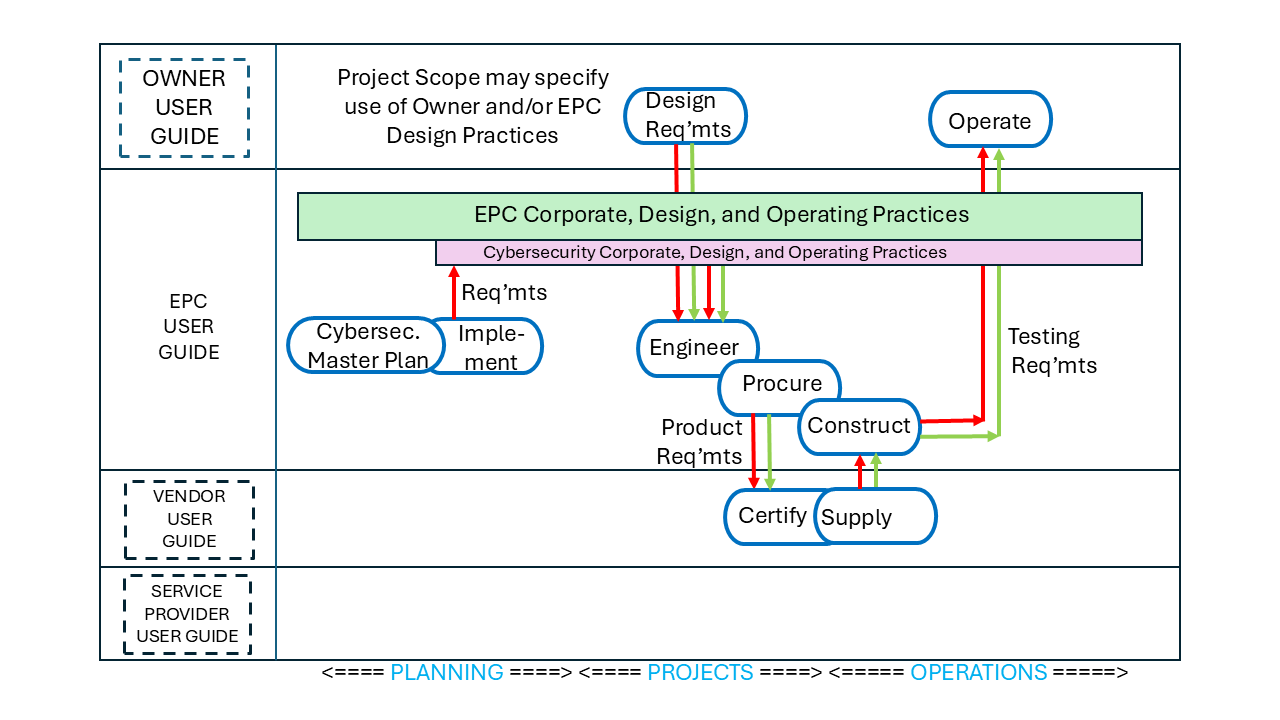
PERA User Guides are available for Process Industy EPCs including::
Each User Guide provides a list of relevant standards, Professional Roles, Typical Opportunities, example Master Planning Reports and other "starter materials" to help with creating the Master Plan.
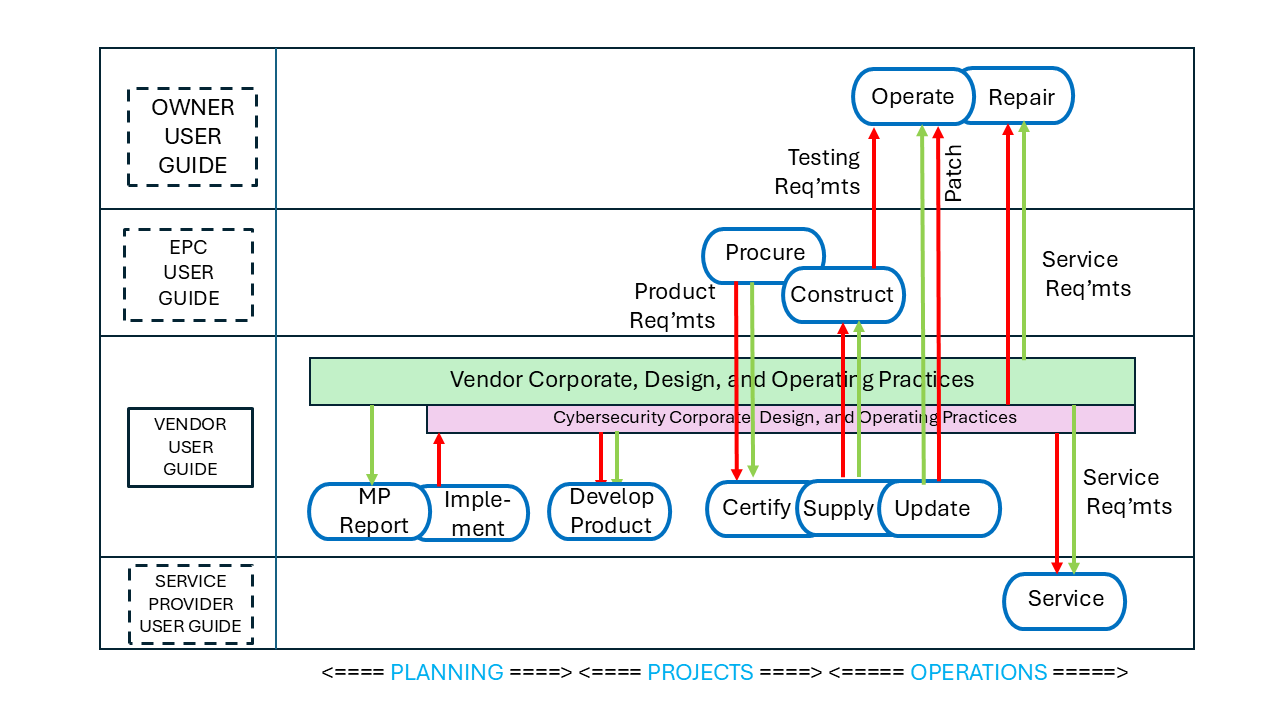
PERA User Guides are available for Process Industy Vendors including:
Each User Guide provides a list of relevant standards, Professional Roles, Typical Opportunities, example Master Planning Reports and other "starter materials" to help with creating the Master Plan.
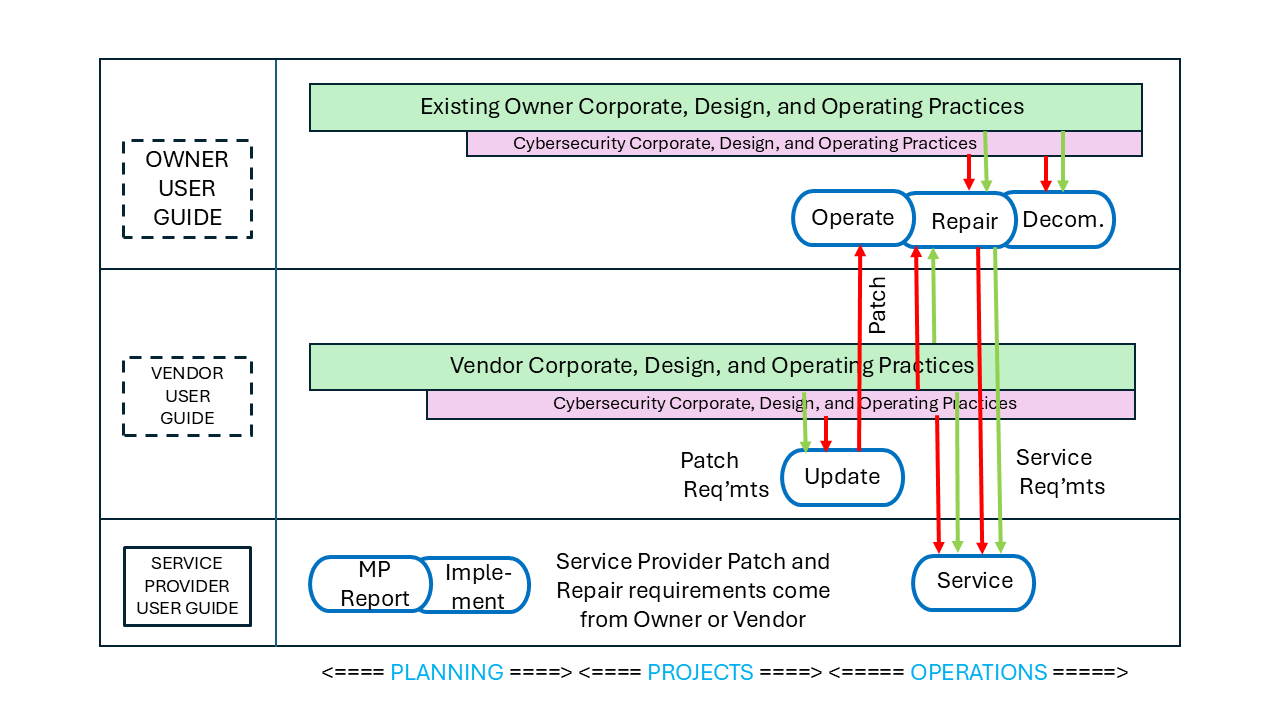
PERA User Guides are available for Process Industry Service Providers including::
Each User Guide provides a list of relevant standards, Professional Roles, Typical Opportunities, example Master Planning Reports and other "starter materials" to help with creating the Master Plan.
Note other Principal Roles may be relevant for that Industry, including Regulators and Standards organizations, Educators, and Insurers. If you have, or plan to develop one or more of these please leave a comment below.